Multi-Factor Authentication
Service
What is Multi-Factor Authentication?
Multi-factor authentication is like a digital fortress. You can only step inside after proving you belong. Show two or more credentials—something you know, something you have, and something you are. It’s your key to safety!
Why we need Multi-factor Authentication for our organization?
MFA is a game changer for your organization’s security. It pushes users to prove their identity beyond just a username and password. Think about it—passwords are like a flimsy lock on a treasure chest. They can be cracked or swiped by sneaky intruders. Why settle for just a password when you can fortify your defences?
Features of Multi-factor Authentication
- Easy to Implement
- Adaptive
- Role-Based Multi-Factor Authentication Tool
- Cloud-Based Multi-Factor Authentication Software
- Multi Authentication Modes
- Hard Tokens & Soft Tokens
- Customizable
Easy to Implement
One of the main hurdles that IT departments of the organizations that are so willing to adopt MFA face is the deployment into the existing identity environments, and especially so when that environment consists of both on-premise and cloud apps. Always be sure to seek out an MFA software that can be deployed on-premises or as a service, and deployment becomes a hundred times easier.
Adaptive
Enterprise mobility and BYOD has made the user to access sensitive information from any location and through any device. Data security and compliance is at high risk. Adaptive multi-factor authentication address this by adding the flexibility to user for accessing their resources with no compromise on security. The MFA tool should feel that user has logged in from different place using different device and should put in front the challenges which a genuine user can only pass to identify him. This will avoid the unauthorized access, if somebody else has got the opportunity to try to access the user’s resources – lost/stolen device.
Role-Based Multi-Factor Authentication Tool
You often have people with different levels of privilege and different roles in an organization. A one-mode-fits-all strategy for user authentication is definitely not the right way to go if that’s the case. The MFA software needs to be able to initiate role-based authentication for different set of users – this will be useful in managing the privileged accounts which have access to sensitive data, and for hardening security.
Cloud-Based Multi-Factor Authentication Software
The count of cloud applications that is getting used in Enterprise or Higher-Ed Institutions in increasing day by day. Be it Email, CRM, ERP, Productivity apps or anything and everything is moving to cloud. Same with MFA too. When you are serving such customers, you can’t ask your customer worry about availability and manageability. Need to be relevant to changing times.
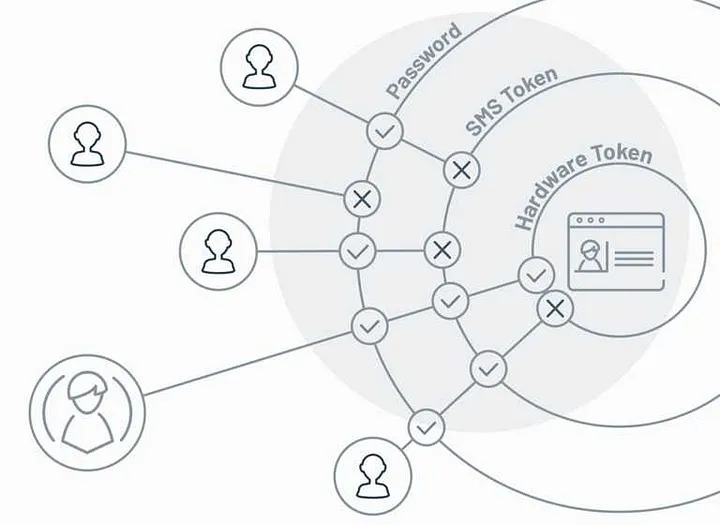
Multi Authentication Modes
Modes of authentication like Email, Phone, Browser Push Notification, Device, Challenge Questions and Touch ID not only provide diverse options to users which they prefer, but also increases the level of security in the applications. Some modes that you need to look out for are: Some modes that you need to look out for are:
- Email Verification – This is an email that a user receives with a link that verifies his account or a code. The user must either click on the link or type the verification code so that the he/she can be allowed to access the resources.
- Phone Verification – OTP(one time password) is sent to the phone number you used at the time of account sign-up and this is required when accessing the account.
- Browser Push Notifications – One gets created on the browser, which helps in pulling the verification code and further aids in the confirmation of the user.
- It can also be noted that Biometrics – Based MFA is most secured authentication method hard to break as discussed below. Biometric identification using finger prints, voice command or even scans that mimic the human retina can be used to identify the users.
Hard Tokens & Soft Tokens
A small piece of device like key fob or smart card transmits a one-time password to the session of the user. The users have to carry the hard token along in order to use this means of MFA. A soft token could be in form of a one-time password that is created by an application or a software to authenticate the user’s identity. More of the organizations prefer using soft tokens as the hard tokens can be stolen or may be lost.
Customizable
The Enterprise IT should have an option for instance to allow end users to manage their device and decide whether to require MFA in the specific device or not. This will result in improved end user capacity and allow them to use various equipment in a secure manner.
