Firewall/UTM/NGFW
Service
What is Firewall/UTM/NGFW?
An integrated weapon system comprising various security features and services that operate in unison on a single device within the network, Unified Threat Management (UTM) is designed to shield users from security threats in a straightforward manner. Functions provided by UTM include Firewall, Antivirus, Antispam, Intrusion Prevention/Detection, Web-Application Control, Sandboxing, Link Load Balance, Bandwidth Management, Client Authentication, VPN and Detailed Reporting.
Why we need firewall for our organization?
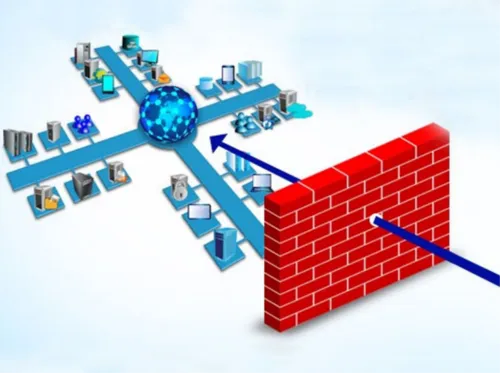
Without a firewall, any request will pass through to vulnerable systems, making it possible for malicious actors to access your computer for their own gain. A firewall blocks unauthorized requests and allows passage only to designated traffic. There are a couple of functions used by the firewall to ensure your servers’ safety, and we will briefly go through them.
What is the importance of having a firewall for our organization?
In the absence of a firewall, any request comes through to the undefended system, which gives an opportunity for hackers to reach your machine for personal benefits. The function of a Firewall is to block unauthorized requests and permit only authorized traffic. The firewall performs several functions that guarantee the security of your servers; let’s take a quick look at them.
Features of Unified Threat Management
- Firewall
- Link Load Balance
- SD-WAN
- Site to Site VPN
- Client/Remote VPN
- Gateway Antivirus
- Web Content Filtering
- Intrusion Prevention System
- Application Control
- Bandwidth Management
- Sand Boxing
- Antispam
- Reporting
Firewall
Firewalls can scan both outgoing network traffic to detect viruses and malware well, as protect against phishing attacks and spam emails that could pose cybersecurity threats to your systems security. This type of firewall known as UTM (Unified Threat Management) is effective in not monitoring data flow but in preventing any devices, within the network from inadvertently spreading malware to other connected networks.
Link Load Balance
Link load balancing involves using a switch to distribute data centre processing tasks and high network traffic volumes across several servers avoiding overburdening any individual device.
SD-WAN
Ensure the safety of users and devices throughout your wide area network (WAN) while making IT operations more efficient. Zero trust session integrity, supported by vector routing and access policies that default to denial are, among the methods we employ to guarantee robust security, with SD WAN.
Site to Site VPN
Using a Virtual Private Network (VPN) individuals can securely transmit and receive data, over public networks by creating a private connection that simulates direct access to a secure network, from their devices.
Client/Remote VPN
With a remote access VPN employees can securely connect to a computer network and access resources as if they were physically connected to the networks servers directly.
Gateway Antivirus
The Cloud Gateway Anti-Virus feature brings in a cutting-edge malware scanning fix. This new solution works with and builds upon the Gateway AV scanning tools already on firewalls. It aims to tackle the ongoing rise in malware samples out there.
Web Content Filtering
Firewalls can scan both outgoing network traffic to detect viruses and malware well, as protect against phishing attacks and spam emails that could pose cybersecurity threats to your systems security. This type of firewall known as UTM (Unified Threat Management) is effective in not monitoring data flow but in preventing any devices, within the network from inadvertently spreading malware to other connected networks.
Intrusion Prevention System
An Intrusion Prevention System’s main jobs are spotting fishy activity writing down key info trying to stop the activity, and then telling someone about it. IPS’s protect against many types of attacks. These include SQL injection cross-site scripting running code from afar, shell code payloads, and remote procedure calls.
Application Control
The application control consists of all these functions like completeness and validity checks, identification, authentication, authorization, input controls, and forensic controls, etc. Application controls, in other words, guarantee that the application and its related data are protected against unauthorized access, modification, and destruction.
Bandwidth Management
Overconsuming of network capacity in one location can have a negative effect on the whole network. Bandwidth issues may also cause the critical business services to be unavailable and result in the network downtime. You are probably just buying more bandwidth to solve the problem, but you are only treating a symptom of a bigger problem.
Sand Boxing
Sandboxing refers to a cyber security practice where you run the code, then observe and analyze the code in a secure, isolated environment on a network that basically imitates the end-user operating environments. Sandboxing is a practice mainly designed to prevent threats from getting onto the network and is often used to examine code that is either untested or untrusted.
Antispam
Anti-Spam Engine is a full filtering solution, which prevents junk mail and viruses from reaching our servers. Your inbox is thus secured from spam and you are saved from spending hours managing unsolicited email. AntiSpam provides easy service from the first installation to the last report.
Reporting
Offers real-time activity tracking of users, monitoring the bandwidth usage, identification of the application, analytics, and forensics flow, compliance and audit reports, scheduled reports, among others.
